
Empowering Your Digital Defense Strategy for a Safer Future.

Hey there! So, guess what? We're Luitech Cyber IT, and we're here to save the day in the big, bad world of the internet! Yep, you heard it
right we're like the superheroes of cyberspace, swooping in to protect your digital kingdom from all the baddies out there.

Fortify Your Defenses Uncovering Essential Elements of Cyber Security.


To address your software issues more efficiently, We offers three distinct packages differentiated by their coverage and spanning L1, L2 and L3 tiers of technical support.
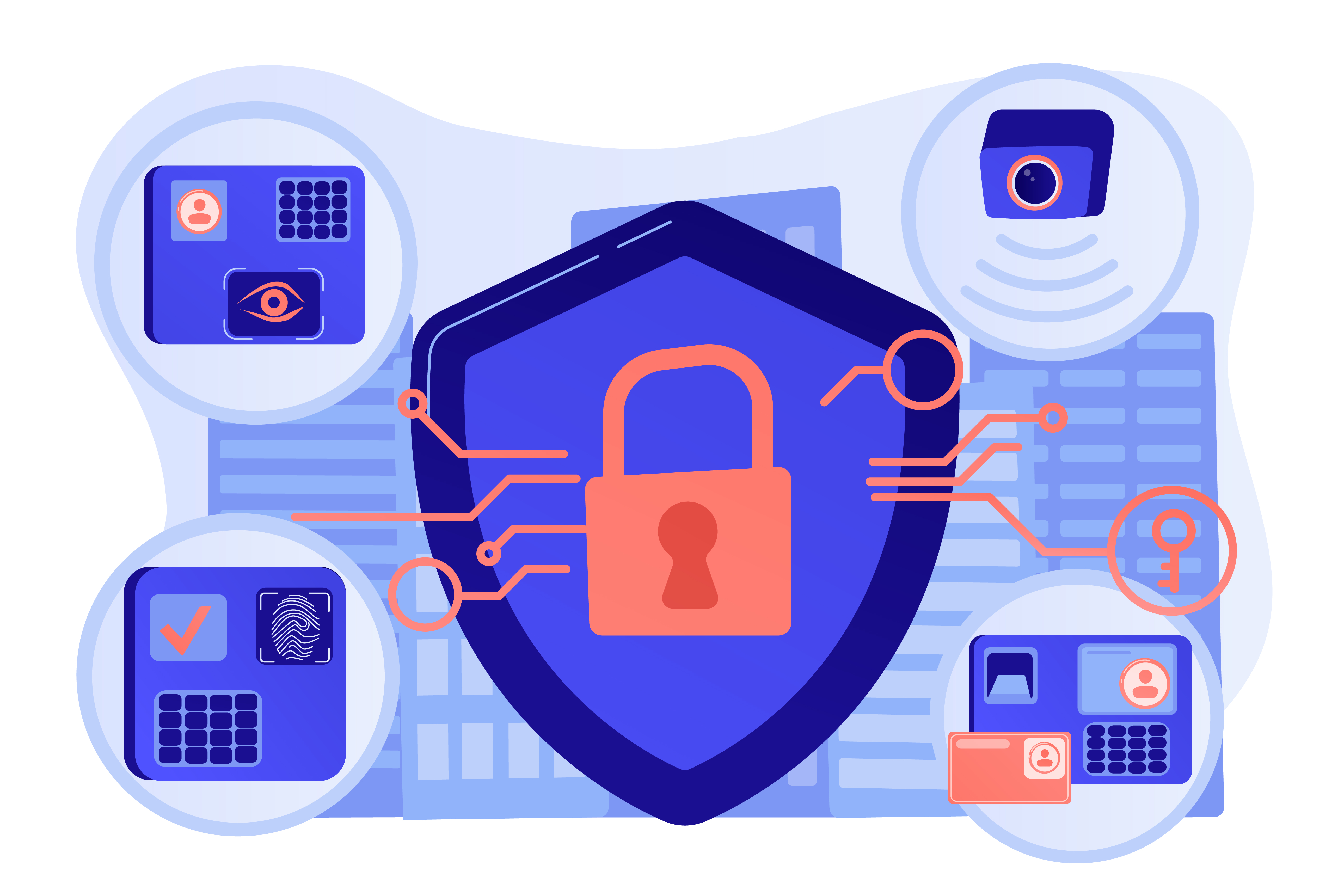
Our services encompass a robust array of defensive measures. We provide strong firewall protection coupled with vigilant intrusion detection to safeguard your network. Our endpoint security solutions offer comprehensive defense against evolving threats. With advanced threat intelligence and continuous monitoring, we stay ahead of potential risks. Additionally, our compliance expertise
ensures adherence to regulatory standards, providing you with comprehensive security coverage.
Our administrative system management platform offers a comprehensive suite of features designed to streamline operations and enhance organizational efficiency. With user management capabilities, administrators can easily add, edit, and remove users, assigning roles and permissions as needed.
Advanced algorithms and threat intelligence capabilities to detect and prevent cyber threats, including malware, ransomware, phishing attacks, and zero-day vulnerabilities.
Real-time monitoring of network traffic and systems for signs of unauthorized access or suspicious activities, coupled with automated responses and incident management workflows.
Robust firewall solutions to safeguard network infrastructure, controlling inbound and outbound traffic based on predefined security policies and filtering out potential threats.
Comprehensive endpoint protection for devices such as computers, laptops, mobile devices, and servers, including antivirus, anti-malware, device control, and application whitelisting features.
Encryption technologies to secure sensitive data both in transit and at rest, preventing unauthorized access or data breaches even if intercepted or stolen.
IAM solutions to manage user identities, access rights, and privileges, ensuring that only authorized individuals have appropriate access to resources and systems.
Tools and frameworks to help organizations achieve and maintain compliance with industry regulations and standards such as GDPR, HIPAA, PCI DSS, and ISO 27001.
Development and implementation of incident response plans, including procedures for reporting, investigating, containing, and recovering from cyber security incidents.
Continuous monitoring of networks, systems, and applications for vulnerabilities and emerging threats, leveraging threat intelligence feeds and security analytics to stay ahead of cyber adversaries.
Specialized security measures and controls for cloud-based environments, ensuring the confidentiality, integrity, and availability of data and applications hosted in the cloud.
Create dynamic quizzes with randomized question pools for varied assessments.Automatically adjust the difficulty levels of questions based on individual student performance.
Managed security services provided by a dedicated SOC team, offering around-the-clock monitoring, threat hunting, incident response, and remediation support.
Automated vulnerability scanning and assessment tools to identify, prioritize, and remediate security weaknesses in networks, systems, and applications.
Web application firewalls (WAFs), secure coding practices, and vulnerability testing tools to protect web applications from common threats such as SQL injection, cross-site scripting (XSS), and injection attacks.
Network segmentation strategies and tools to partition networks into separate zones or segments, reducing the attack surface and limiting the spread of malware or unauthorized access.
SIEM platforms that aggregate, correlate, and analyze security event logs and data from various sources, providing insights into security incidents and facilitating rapid incident response.
On-demand product designed to accelerate your product development.

We've curated a talented group to solve startup challenges, saving you the hassle and cost of assembling your own team.


Hi-Tech professionals with having years of experience excel in rapid deployment and product shipping—no matter the time zone.
We bring all of the necessary skills to take your product to the next level. Product strategy, startup coaching, system architecture, UX/UI design, branding and go-to-market, to name just a few.


Focus on meeting business outcomes with market leading software.

Adapt as ideas evolve without costing extra.

Optimize for team cohesion and speed.

Know how to capitalize on each other's strengths.


Focus on meeting business outcomes with market leading software.

Adapt as ideas evolve without costing extra.

Optimize for team cohesion and speed.

Know how to capitalize on each other's strengths.